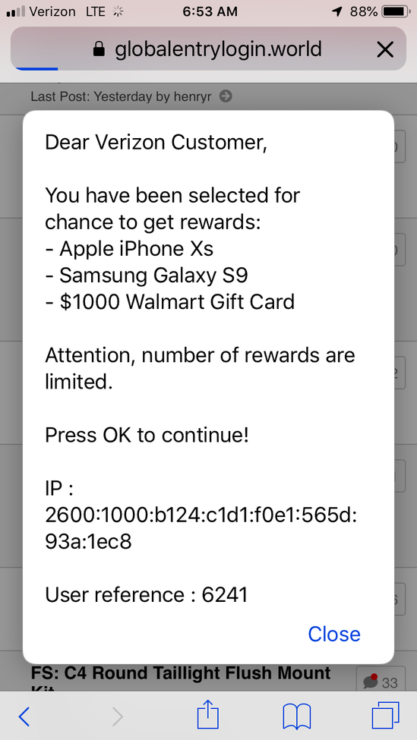
It has come to light that about 500 million fake ads were pushed out to iPhones in the United States in early April. It was confirmed by researchers at ad-verification firm Confiant and fears another campaign onslaught for the upcoming Easter weekend. The hijack exploits an unpatched flaw in the Chrome for iOS browser which bypasses the sandboxing and takes over user sessions targeting iOS devices. The hijack is the work of the eGobbler gang which has a solid track record of releasing large-scale malvertising attacks ahead of major holidays. Let’s dive in to see some more details on the nature of the attack.
Chrome For iOS Security Sandbox Fails Resulting In Malvertising Campaign Affecting Half A Billion iPhone Users
Since Easter is coming up, a plethora of users will be surfing the web on their iOS devices and it sounds like the best time for the eGobbler team to release another wave of malvertising. Session hijacking is the process where a webpage automatically redirects to another site or the landing page. Moreover, it can also be a pop up that users can’t exit. On the front, the ads showcase well-known brands and if by any chance a user clicks on it, a payload is released.
In this scenario, the campaign remains active under the ‘.site’ TLD landing pages as per the analyst, Eliya Stein of Confiant. As it seems, the attack is mostly oriented towards users residing in the United States. Apart from this, another research firm has stated that the eGobbler attack is also in effect to impact Safari users as well. This puts an even stronger threat as most iOS users use the stock Safari browser, which is preinstalled on all iOS devices.

The malvertising campaign has been active for the past few days and the reach it gathered is astonishing. Google is aware of the bug in Chrome for iOS, as per the analysis. Confiant researched were surprised on the shift from using pop-ups instead of redirects. This is due to the fact that pop-ups are very rarely seen as part of the hijacking mechanism.
“We tested the payload across over two dozen devices, both physical and virtual,” Stein said. “The malicious code itself has hard-coded logic that targets iOS, so we removed that condition in order to see the results of the full execution on all of the devices that we tested…Right away we were surprised to find that the payload’s main session hijacking mechanism was pop-up based, and furthermore, Chrome on iOS was an outlier in that the built-in pop-up blocker failed consistently.”
Since pop-ups are not preventable by the standard ad sandboxing properties in Chrome for iOS, the blocker was failing. These attributes basically act as the guidelines which are implemented to an iFrame in an attempt to prevent the actions and APIs available to the content.
“These restrictions can include directives like disallowing JavaScript or blocking top level navigation unless prompted by user action,” Stein explained. “Sandboxing tends to have a pretty substantial impact as far as malicious ad mitigation is concerned.”
The eGobbler exploit bypassed most of Google’s standard set of sandboxing attributes upon testing.
“The fact that this exploit is able to bypass that need for user interaction should be impossible according to the same-origin policy as it pertains to cross-origin iFrames,”
“Furthermore, this completely circumvents the browser’s anti-redirect functionality, as the attacker no longer needs to even spawn a redirect in order to hijack the user session.”
Confiant is not yet releasing any details regarding the payload or any other aspect since Google has been notified of the whole fiasco and is working on fixing the exploit as soon as it can. Until the search engine giant releases a fix, the malvertising campaign continues.

There will be more to the story, so be sure et stay tuned in for more information regarding the matter. What are your thoughts in the eGobbler malvertising campaign? Let us know in the comments section below.


